It’s every Database Administrator’s nightmare to see your company’s name in the headlines in connection with a high profile data breach. Breaches can happen to businesses of all sizes and across industries. According to the Verizon’s report, 2015 Data Breach Investigations Report, there was an estimated 2,122 confirmed data breaches in 2014 resulting in $400Million in losses. These figures do not count breaches that were not reported or confirmed. In addition, breaches can go undetected for months or years before an organization is aware of the issue. A 2013 Trustware survey of 450 breaches and thousands of penetration tests and scans revealed that the average time between initial breach and detection was 210 days; that’ up from 90 days in 2010. The delay in discovering a breach further exacerbates the problem.
The average cost to an organization for a lost or stolen record has steadily increased in the last two years from $188 to $201. We are a long way from the days where the lone hacker committing one-off attacks. According to a recent Ponemon Institute Survey, 84% of Financial Services and 44% of Retail firms are experiencing more than 50 attacks per month. Juniper Research estimated that the annual cost incurred from malicious attacks and breaches worldwide will reach $2Trillion by 2019 and that US will account for 80-90% of that figure.
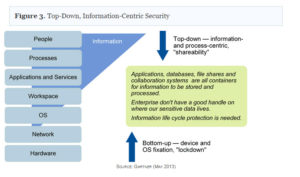
Given the nature and the high frequency of these attacks and changing dynamics in IT where IT doesn’t always own/control consumption or delivery side of technology (as evident in initiatives like Bring Your Own Device and cloud services), a new model of information security is needed. There is a need to shift strategy from a pure bottom-up approach of controlling device and environment to a top-down information and process centric approach to protect information.
This requires employing active monitoring and collaboration across different IT and business functions in an enterprise to protect information assets, build strong detection methods and to develop an incident response plan and team to re-mediate the issue in a timely fashion. (Gartner – Prevention is Futile in 2020: Protect Information via Pervasive Monitoring and Collective Intelligence). There is a strong case for active monitoring/ pervasive monitoring to proactively evaluate and track who is doing what, when, where and how with sensitive data and alerting the right team to investigate further and take necessary action. In addition, a monitoring tool will not only allow you to monitor and create alerts but also to collaborate with different types of users.
Here in the PM group at Idera, we are closely watching these trends as we develop the roadmap for SQL Compliance Manager and SQL Secure. Do you have anything you like to share with us? Let us know in the product forums!