The principle of least privilege is a foundational concept in database security that advocates for granting users the minimum level of access necessary to perform their duties. By restricting user permissions, organizations can minimize the risk of unauthorized access and potential data breaches. This is particularly important in SQL Server environments, where sensitive data is frequently stored and accessed. Implementing least privilege ensures that only authorized individuals can access critical data and system functionalities, reducing the likelihood of security vulnerabilities.
Addressing the Principle of Least Privilege
To effectively address the principle of least privilege, database administrators (DBAs) must conduct thorough assessments of user roles and permissions within the SQL Server environment. This involves evaluating the specific needs of each user or group and adjusting access rights accordingly. By regularly reviewing and updating permissions, DBAs can ensure that users have the appropriate level of access for their tasks. Additionally, implementing tools that monitor and audit access logs can help identify any deviations from the principle of least privilege, allowing for prompt corrective actions.
Impact on SQL Server Security
Implementing the principle of least privilege significantly enhances SQL Server security by reducing the attack surface and limiting the potential damage from compromised accounts. When users have restricted access, the chances of accidental or malicious data modification are minimized. This approach also helps in identifying security breaches quickly, as any unauthorized access attempts are more easily detected when access permissions are tightly controlled. By prioritizing least privilege, organizations can protect sensitive information and maintain compliance with data protection regulations.
Implementing Least Privilege with IDERA Tools
IDERA’s suite of SQL Server tools, such as SQL Secure and SQL Compliance Manager, can assist DBAs in implementing the principle of least privilege. SQL Secure offers comprehensive security analysis, allowing DBAs to assess and enforce appropriate user permissions across the SQL Server environment. Meanwhile, SQL Compliance Manager provides detailed auditing capabilities, ensuring that all access and modifications are tracked and logged. By leveraging these tools, organizations can efficiently manage user access and bolster their SQL Server security posture.
Minimum Security Permissions Required for SQL Compliance Manager to Work
Requirements: To be able to use SQL Compliance Manager with minimal privileges
Existing design
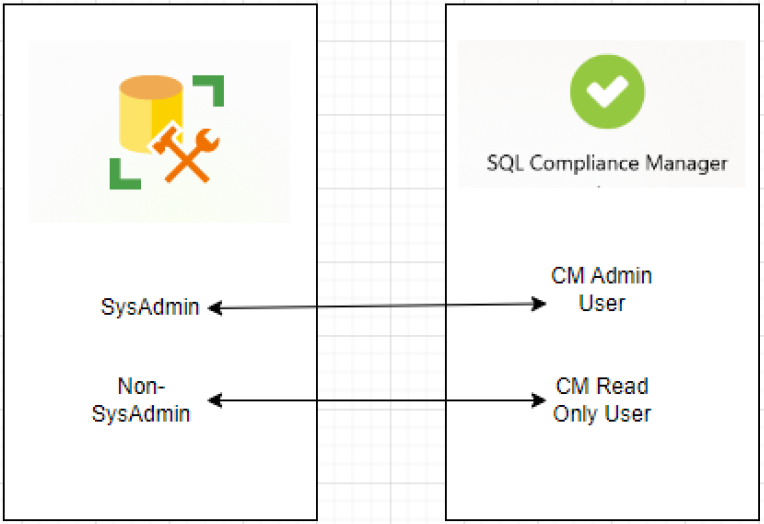
Currently, the SQL Compliance Manager permission model mirrors the permissions of the SQL Server. Any changes made on the Compliance Manager side were reflected on the SQL Server level. The feature being implemented tries to decouple the SQL Compliance Manager permissions with the SQL Server permissions.
The changes to the logins through SQL Compliance Manager are also taking effect at the server level.
The public role was given a lot of grants on objects in relation to SQL Compliance databases as well as master database.
New design
For this new approach, SQL Compliance Manager is working without sysadmin permissions and makes the SQL Compliance Manager permission model independent of the SQL server.
SQL Compliance Manager no longer needed to be a sysadmin
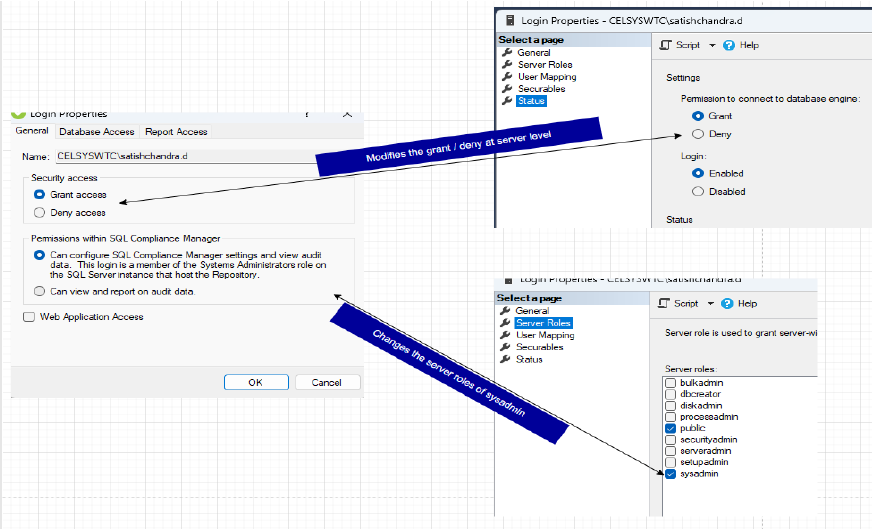
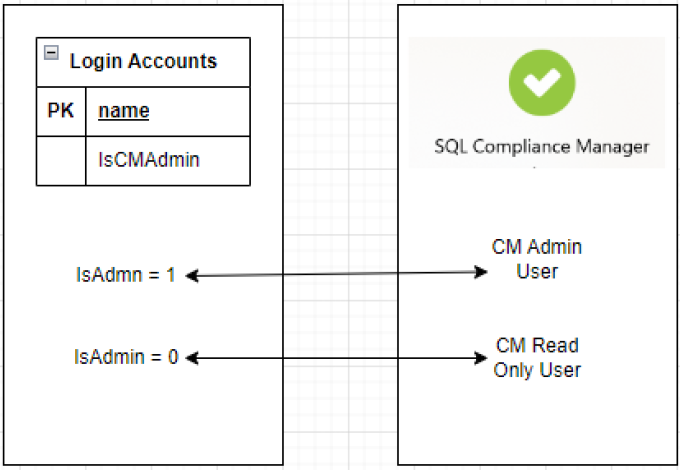
Previously a SQL Compliance Manager admin was also a sysadmin on the SQL Server. As per the latest design a non-sysadmin login can also be a SQL Compliance Manager Admin. A Permissions Manager class has been introduced to handle the permissions requirements of various features in SQL Compliance Manager as per the privileges of the logged-in user.
The privilege level of a login with respect to SQL Compliance Manager (CM Admin / CM Read-only) is now stored in the Login Accounts table of the SQL Compliance database and is not related to sysadmin permissions. Some features are still needed for the elevated permissions to work as designed. Such as when a user with less-than-required privileges tries to access such features, a warning will be presented that the action needs more privileges.
Grant/Deny permission to take effect at database level
When the user tries to grant access or deny access we are now reflecting the setting at the database level by denying the access to the database (unmapping the selected user from the SQL Compliance databases)
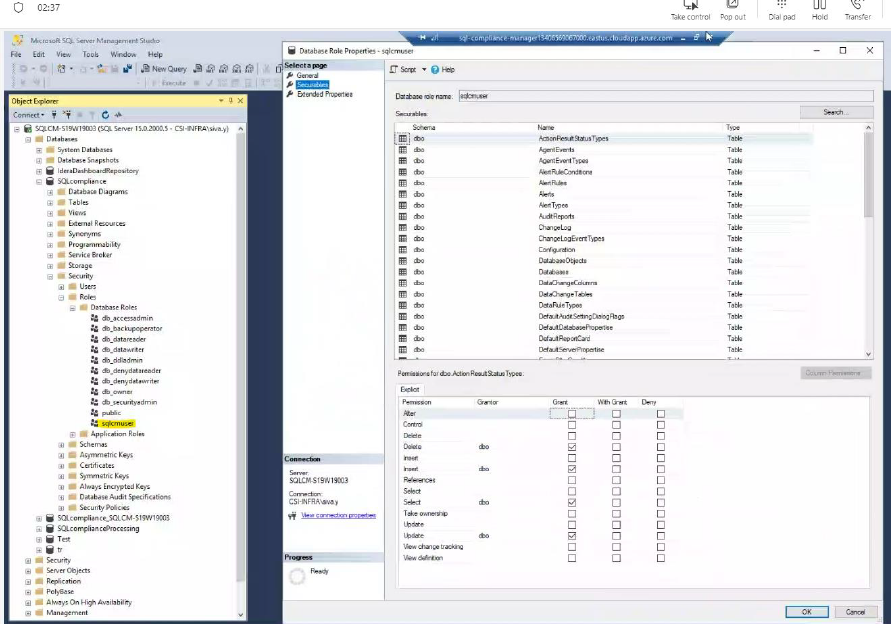
Public role to have no/minimal grants related to SQL Compliance Manager
All grants that are given to the public role are now moved to a dedicated role called sqlcmuser. This role will be created at the time of a fresh installation as well as an upgrade and all grants will be provided for this role.
Note: When a new user is added from SSMS, SQL Compliance Manager needs to be launched with a user that is a sysadmin to add the required permissions for the new login.