Recently a security issue allowing allowing local code execution after visiting a malicious URL was identified in Subversion, git and Mercurial. All three source control systems released a synchronised security update.
In RAD Studio, we use an external installation of both git and Mercurial, which you point the IDE to in the Options dialog. (Tools > Options > Version Control, and then either the git or Mercurial subitems.) Update whichever distribution you use.
However, we do ship Subversion DLLs, which could be affected by this issue. These can be easily updated, and we have internally tested new DLLs against RAD Studio 10.2.1. You can find full instructions in the readme.txt in the \bin\subversion folder – for me this is C:\Program Files (x86)\Embarcadero\Studio\19.0\bin\subversion . A rough summary is:
- We test against builds from collab.net, and use the 32-bit binaries. If you use different binaries, you may end up with different DLL names which the IDE will not recognise. For this post, I downloaded "Subversion 1.9.7 (Windows 32-bit)". Make sure you virus-check or take other appropriate precautions as you would from any website, despite collab.net being well-known.
- If you overwrite the DLLs in the folder above:
- Please close the IDE first
- Back up the existing DLLs before replacing them
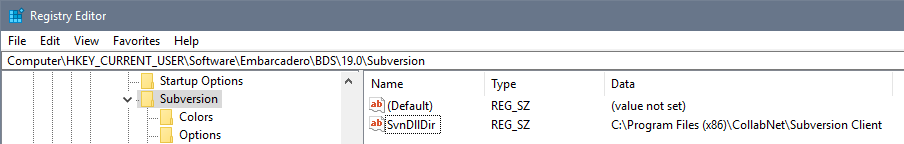
- You can also install to any folder, and redirect the IDE. Do this only if you are confident editing the registry.
- Please close the IDE first
- In the registry, navigate to HKEY_CURRENT_USER\Software\Embarcadero\BDS\19.0\Subversion
- Create a new string value called "SvnDllDir" (without quotes), and set its value to the path you installed the DLLs to. You do not need a trailing slash.
The readme file has full details.