Last week I spoke at DAMA Day in NYC. The day was focused on GDPR and all of the implications in the regulation. I decided to focus my talk on why Data Breach is such a big deal that it has its own articles included in the GDPR Regulation.
Data Breach by the Numbers
- Over 5 million records are lost or stolen every day
- Two Billion Files containing personal data of US Citizens were leaked in US Data Breaches in 2017
- The median number of days that attackers stay dormant within a network before detection is 200 days
- The average cost of a single data breach in 2020 will exceed $150 million as more business infrastructure gets connected
Data Breaches in the US in 2017 alone
- Healthcare (60% of all leaks)
- 328 breaches
- $1.2 Billion
- Technology
- 48 breaches
- $1.2 Billion
- 1.8 Billion records
- Finance
- 40 breaches
- $144.8 Million
- 146 Million records
- Retail
- 40 breaches
- $144K
- 4.7 Million records
Small Business Data Breach Numbers
- 90% of data breaches impact small businesses
- 60% of data breaches target small businesses directly
- 90% of small businesses don't use any data protection at all
- Attacks cost small businesses between $84k and $148K
- 31% of customers terminated their business with the small business after being notified of a breach
- 60% of small businesses close their doors permanently within 6 months of experiencing a data breach
Individual Concerns over Data Security
- By 2020 over 30 Billion devices will be connected to the internet
- 49% of Americans feel that their personal information is less secure than it was five years ago
- Over 73% of consumers in America want companies to be transparent about personal data
- 78% of people claim to be aware of the risks of unknown links in emails, yet click on those links anyway
- 86% of internet users are actively trying to minimize, anonymize and hide the visibility of their digital footprints
Data Security Preparedness
- In 2014 70% of Millennials admitted to bringing outside applications into the enterprise in violation of IT policies
- 52% of organizations that suffered successful cyber attacks in 2016 aren't making any changes to their security in 2017
- Only 38% of global organizations claim they are prepared to handle a sophisticated cyberattack
- Only 37% of organizations have a cyber incident response plan
Data Security from an Executive Perspective
- 90% of CIOs admit to wasting millions on inadequate cybersecurity
- 90% of CIOs have already been attacked or expect to be attacked by bad guys hiding in their encryption
- 87% of CIOs believe their security controls are failing to protect their businesses
- 85% of CIOs expect criminal misuse of keys and certificates to get worse
What are the Odds of a Breach?
- 1 in 960,000 – odds of being struck by lightning
- 1 in 220 – odds of dating a millionaire
- 1 in 4 – odds of experiencing a data breach
The 2017 Cost of a Data Breach
- The average cost for each lost or stolen record containing sensitive and confidential information was $141 (a 10% decrease from the year before)
- The average size of a data breach was 24,000 records (an increase of 1.8% from the year before)
- $141 x 24,000 ~ $3.4M
Some of the specific Data Breach costs
- Forensic analysis to determine the extent of the breach
- $200 to $2000 an hour for specialists to review the data
- Written notification to affected customers
- $5 to $50 for each customer
- Credit monitoring for affected customers
- $10 to $30 for each customer
- Legal defense costs
- Between $500K and $1M are typical
- Regulatory fines and judgments
- Target paid $18.5M after a 2013 breach affecting 41M customers
- Reputational losses
- 20% of regular customers allowing for 30% of revenue
Ways to drive down the costs
For the $141 per record breached, you can reduce your cost by:
- $19.30 – create an incident response team
- Saves money by containing the event quickly
- $16.10 – extensive use of encryption
- Saves money by restricting access to the information
- $12.50 – employee training
- An educated workforce helps plan for potential threats before they happen
What does GDPR say about Data Breaches?
Data that must be protected
Any information that can be classified as personal details – or that can be used to determine your identity
- Name
- Identification number
- Email address
- Online user identifier
- Social media posts
- Physical, physiological or genetic information
- Medical information
- Location
- Bank details
- IP address
- Cookies
Article 33 – Notification of Personal Data Breach to the Supervising Authority
- Detect breaches
- Assess the impact on personal data records
- Assess whether the personal data is identifiable
- Describe the nature of the breach
- Describe your measures to remedy it
- Alert Supervising Authority within 72 hours of the breach
How do you set up your Data Breach processes?
Breach detection response planning
- Plan for the attack (it is coming)
- Know what your response will be and train all applicable employees on it
- Detect access quickly
- Enable tools that will allow you to be able to detect the breach and know what information was access
- Create a detection response team
- Internal or retained, create a team that can act immediately
- Establish a communications plan
- Knowing exactly what you will say allows you to spread the word quickly and lessen the confusion
Safeguarding personal data
- Identify which data is Personally Identifiable Data
- Map the data in existing systems to reduce redundancy
- Keep only the data that you absolutely need
- Determine when the data should be made available
- Restrict access to only those who should have access
- Minimize the places where data is stored
- Set data encryption levels while:
- In Use
- In Transit
- At Rest
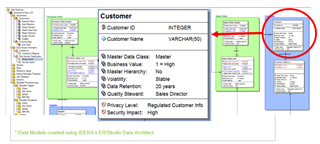
Identifying data security properties in your data models
ER/Studio Data Architect allows you to set security impact directly in your data models so that you can start keeping track of these elements from the very beginning of your data design processes. Additionally, you can reverse engineer your existing data models and use ER/Studio Data Architect and Team Server to help to identify these elements.
Mapping data to reduce redundancies
You can use ER/Studio Business Architect to start to draw out mappings between tables and systems. Additionally, in ER/Studio Data Architect you can set up Universal Data Mappings within the repository that will help you to map together from a host of implementations. ER/Studio Data Architect also allows you to leverage entity editors to link related objects across models.
Removing these redundancies allow you to better identify what information was accessed in the case of a breach. If it is spread out across a variety of tables it makes it more difficult to determine which system had the breach.
Determine when data should be available
You should map out your business processes using a tool like ER/Studio Business Architect to determine when data should be made available to systems rather than allowing full access which could make you vulnerable during a data breach.
Restrict user access
Using tools like ER/Studio Business Architect you can define subject areas within your data and lock down access to those subject areas to only the people who need it. It's also a good practice to identify a main person who is responsible for that subject area who can make decisions that impact that data. This person should have an approval/change management process in place to ensure that they know at all times who is accessing their data and locking out those who should not be accessing it.
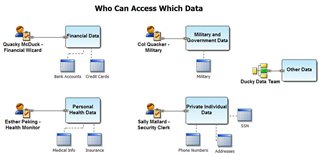
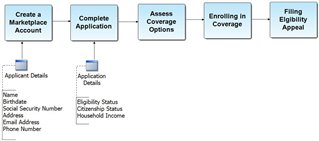
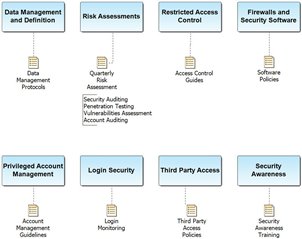
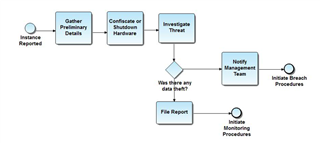
Other questions to consider
- What are your procedures for handling PII Data?
- What security protocols are in place to protect the data?
- How will you respond to a data breach?
- How do you detect that a breach is occurring?
- How will you notify affected customers?
- How will you train your teams on your processes?
Below are a few example Business Process Diagrams that have been created in ER/Studio Business Architect that can help to get conversations started in your own organization.
Handling PII Data
Establishing Security Protocols
Responding to a Data Breach
Detecting a Breach in Progress
Data Breach Notification
In Conclusion
- Data breaches are common and will continue to become more common
- While companies improve their data breach processes, costs continue to climb
- Because data breach processes are so common, GDPR is taking deliberate steps to ensure that companies take serious efforts to protect people’s personal information
- Knowing what to do in the case of a breach will help to drive down costs should a data breach occur
- There are tools out there that can help you limit your chances for breach and help you quickly detect and respond to a breach should it occur
IDERA products for GDPR preparation
- ER/Studio Enterprise Team Edition can help you to document your data processes and incorporate data standards into your data architecture
- SQL Compliance Manager can help to detect breaches and audit your information to make sure that the wrong people aren’t accessing your data
- SQL Safe Backup can help to encrypt the data in your backups
- SQL Inventory Manager can verify that your servers are patched and up to date
- SQL Secure can audit privacy and encryption standards
Download a trial copy of our products at https://www.idera.com/
GDPR Whitepapers
GDPR Blogs
Statistic Source Links:
-
https://www.infosecurity-magazine.com/news/two-billion-files-leaked-in-us-data/
-
https://swimlane.com/10-hard-hitting-cyber-security-statistics/
-
https://analyticsweek.com/content/whats-the-true-cost-of-a-data-breach/
-
https://www.firstdata.com/downloads/thought-leadership/Small_Businesses_Cost_of_a_Data_Breach_Article.pdf
-
https://www.usatoday.com/story/money/columnist/strauss/2017/10/20/cyber-threat-huge-small-businesses/782716001/
-
https://www.wired.com/insights/2014/09/millennials-mobile-security/
-
https://www.venafi.com/assets/pdf/wp/Venafi_2016CIO_SurveyReport.pdf
-
https://www.juniperresearch.com/press/press-releases/cybercrime-cost-businesses-over-2trillion
-
https://securityintelligence.com/know-the-odds-the-cost-of-a-data-breach-in-2017/
-
https://www.ibm.com/security/data-breach
- Data Privacy Day
- National Cyber Security Alliance and Zogby Consumer Poll
- Pew Research Center
- PWC Economic Crime Sruvey