The cloud these days not only offers virtual machines and storage, but also brand new and exciting services such as the cognitive services. You need...
database-tools
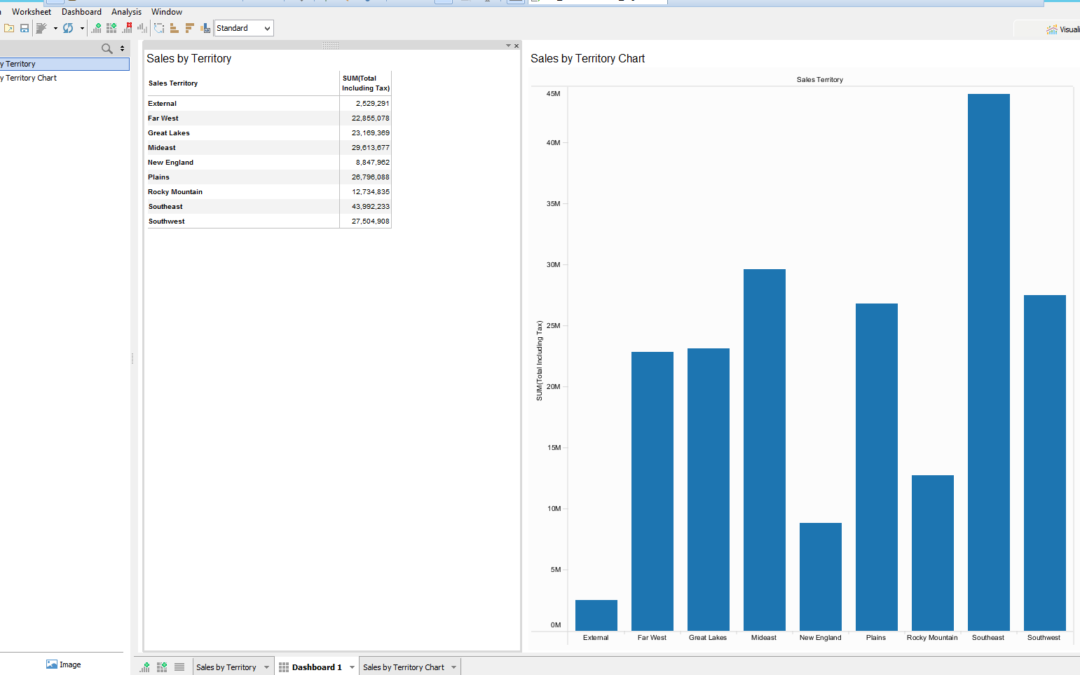
How to Build Effective Data Visualizations
A tool like Aqua Data Studio provides a rich canvas for creating data visualizations. While these charts, graphs, etc. can be eye candy, without...
Backing Up All Scripts to ZIP
PowerShell 5 finally includes support for ZIP files, so if you want to backup all of your PowerShell scripts into one ZIP file, here is a one-liner:...
Running PowerShell Code as Someone Else
Local admin privileges are extremely powerful, and you should use techniques such as JEA to minimize the number of local Admins as much as you can....

Announcing SQL Safe Backup 8.5.1 General Availability
We are pleased to announce the general availability of SQL Safe Backup 8.5.1. Existing users may upgrade to this version through the IDERA Customer...
Hardening Script Block Logging
By default, script block logging data is open to anyone, not just Administrators. When script block logging is enabled, any user can access the log...
Enabling Script Block Logging
In the previous tips, we took a deep look at how PowerShell 5 script block logging works: in a nutshell, when enabled, all PowerShell code that...
Finding Secret Passwords in Memory
Some scripts may leave variables with sensitive information behind. This can happen by accident, when the global scope is used, or when users call...
Outputting Data to HTML Reports
Here is a super easy and useful PowerShell function called Out-HTML: function Out-HTML { param ( [String] $Path = "$env:temp\report$(Get-Date...
Stealing Sensitive Data from PowerShell Functions
Frequently, PowerShell functions work with sensitive information, i.e. log-on information including passwords, and store this information in...

IDERA Honored in DBTA’s “Big Data 50” List
We’re proud to announce that for the second straight year IDERA was named to the “Big Data 50” list published annually by...

October #SQLChat: Making the Most of Conferences – From Training to Networking
So you're attending a training conference next month. Maybe you're a first timer, maybe this is your 10th year. Making sure you...
Handling Credentials as Parameters
Credentials are objects that contain a user name and an encrypted password. If your PowerShell functions should be able to accept credentials,...
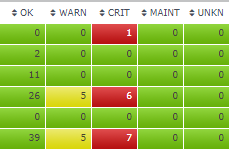
Attention Operational DBAs
Uptime Database Infrastructure Monitor triages large environments so that you can quickly determine what needs your immediate attention, Database...
Resolving Mapped Drive
Ever wanted to know the original URL behind network drives? Here is an easy PowerShell way: # make sure the below drive is a mapped network drive #...

Data Breaches Are Common – Are You Prepared?
October is National Cybersecurity Awareness Month. In preparation for that, I thought I might take a moment to ponder some security issues...

The Simple 3-2-1 Rule for Backups
Earlier this month, one of Microsoft's Azure data centers encountered an outage that impacted customers worldwide. Microsoft recently...
Downloading Data with BitsTransfer in the Background
Downloading very large files can be a challenge because the download process may take longer than a machine is turned on. With BitsTransfer, you can...
Downloading Data via SSL and BitsTransfer (Sync)
A very convenient built-in way to download files, even with SSL connections, is Start-BitsTransfer. It also sports a progress bar that shows the...
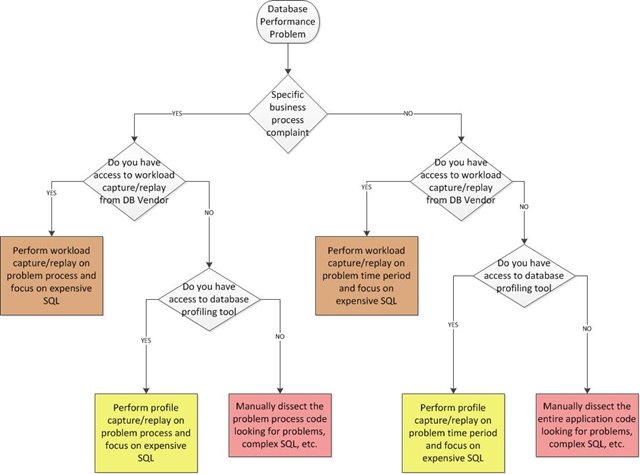
Fixing Database Performance Problems
(content originally posted by Bert Scalzo on 3/8/2017) There is no such thing as the perfect database. No matter how hard the DBA may try, something...
Downloading Data via SSL and Invoke-WebRequest
Invoke-WebRequest can download files for you but may struggle with HTTPS URLs. To use SSL connections, you may have to change a default setting....
Finding Disabled GPOs
Here is a quick one-liner that dumps all Group Policy objects that have all settings disabled: Get-Gpo -All | Where-Object GpoStatus -eq...
Browsing All Event Logs
Get-EventLog always requires you to specify exactly one event log via -LogName. You cannot use wildcards, and you cannot browse all event logs at...
Creating Event Log Reports
You probably have used Get-EventLog frequently to dump event log information, for example: PS> Get-EventLog -LogName System -EntryType Error...