Windows maintains a log file named cbs.log in $env:windir\logs\cbs. It logs various pieces of information related to the Windows trusted installer,...
database-tools
Cleaning Week: Deleting Log File Backups
In a previous tip you learned that there may be gigabytes worth of log file CAB files. Today, let’s try and have PowerShell do the cleanup....
Cleaning Week: Finding Fat Log File Backups
When you run a Windows box for a couple of months or even years, a lot of disk space can be wasted by backed up log files that are not needed. So if...
Cleaning Week: Deleting TEMP Files
In a previous tip you learned how to check for left-over files in both your own temp folder and the one maintained by Windows. Today, let’s...
Cleaning Week: Find Data Garbage
This week is cleaning week, and we’ll show you tactics how you can potentially retrieve gigabytes of disk space, especially with machines that...
Finding Paths to Special Locations
If you’d like to access any of the following special locations, then we have good news for you: PS C:\>...
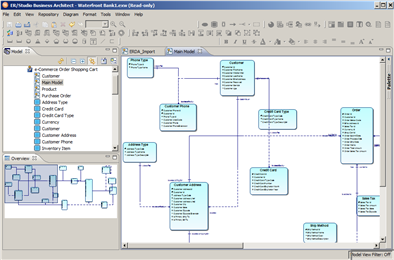
ER/Studio Business Architect – Conceptual and BPMN made Easy!
Howdy! As some of you are aware with the Enterprise Team Edition, comes bundled, Business Architect and Software Architect. Business Architect is...
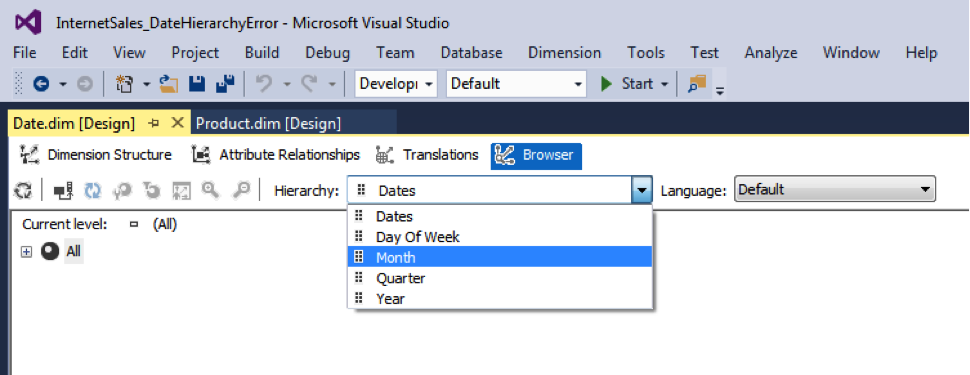
Why use a Date Dimension Table in a Data Warehouse
In the Data Mart, or the Data Warehouse world, there is a date dimension table in all schemas if you are using the Kimball Dimensional Modeling...
Copy Over PowerShell Remoting Sessions
You can use PowerShell remoting to transfer files across a network – this is new in PowerShell 5.0. This can be useful in closed environments...
One-Liner Random Password Generator
Check out this simple way of creating temporary passwords: -join...
Harvesting Reboot Time from EventLog
In the previous tip we illustrated how you can ask WMI for the last reboot time of a machine. A more robust way is to query the Windows event logs....
Last Bootup Time with Get-CimInstance
These days, computers hibernate or go into standby but do not really reboot that often anymore. To find out when your computer rebooted the last...

Get Started with Execution Plans in our June #SQLChat!
Our next #SQLChat will be held Wednesday, June 8 at 12 PM Noon CT with IDERA ACE, Thomas LeBlanc (@TheSmilingDBA). We will be discussing how to get...
Extracting Text Information
Tracert.exe tells you the hops your data packages need to take to get to a given host. Here is an example: PS C:\> tracert www.microsoft.com...
Bulk-Convert to String
Sometimes, commands and methods do not return exactly what you are after. If you, for example, wanted to get the assigned IP addresses for a...
Create Local Admin Accounts
There is no module available for all PowerShell versions that allows to administer local user accounts. Here is a chunk of sample code that...
Loops and Arrays (and some surprises)
Frequently, loops are used to retrieve (or generate) data, then save it to a variable. There can be tremendous performance differences though. To...
Finding Top 3 (of anything)
Ever wanted to know who are the three worst sources for errors in your System event log? Here is a simple approach that yields the source names with...
What Data Modeling Myths Were Uncovered in our #SQLChat?
IDERA hosted its 11th #SQLChat on Wednesday, May 11th with data modeling guru, Karen Lopez (@datachick). The myths and misunderstandings that...
Converting Fixed-Width Text Data
PowerShell can turn fixed-width tabular data easily into rich objects. First, define the column widths. Then, have PowerShell inject a delimiter at...
Exclude Properties
With Select-Object, you typically include the object properties you want to receive. You can do it the other way around, too, though. Here is an...
Creating Temporary Passwords
A good temporary password should be complex, yet unambiguous. So it should contain a mixture of upper and lower case plus special characters, but it...
Beeping PowerShell
Your colleague went to lunch again without properly locking his computer? Then this is your chance to run this code on his PowerShell: $powershell =...
Controlling Return Values
In the previous tip we explained why functions can have multiple return values, and that anything you leave behind will be added to the return...